Introduction: The Case for a Kubernetes-Native Engine
Managing Kubernetes governance at scale introduces significant operational friction. While policy-as-code is the established solution, many engines introduce complexity through proprietary Domain-Specific Languages (DSLs), creating a steep learning curve and hindering developer velocity. Kyverno distinguishes itself as a truly Kubernetes-native policy engine, architected to leverage native tooling and streamline the developer experience. By defining policies as standard Kubernetes resources, it eliminates the need for separate languages and integrates seamlessly with familiar tools like kubectl and Git, thus lowering the barrier to adoption for platform and development teams alike.
This article dissects the three core architectural pillars that enable Kyverno's efficiency and power at scale. First, we will explore the strategic adoption of the Common Expression Language (CEL), which allows for writing expressive, in-line validation rules directly within policy definitions, eliminating the context-switching required by external DSLs. Second, we will analyze Kyverno's deep integration as a dynamic admission controller, detailing how it intercepts API server requests to enforce policies in real-time without complex sidecars or out-of-band processes. Finally, we will examine the advanced automation capabilities unlocked by the GeneratingPolicy resource, demonstrating how it facilitates declarative resource creation and modification, a critical component for robust GitOps workflows. This deep dive will illuminate how Kyverno’s design choices directly address the inherent challenges of policy enforcement in complex, multi-tenant environments.
The CEL Advantage: A Unified Policy Language
Kyverno’s strategic adoption of the Common Expression Language (CEL) provides a significant advantage over policy engines that rely on proprietary Domain-Specific Languages (DSLs). Unlike OPA’s Rego, which introduces a steep learning curve, CEL is already an integral part of the Kubernetes ecosystem. As Kelsey Hightower noted, "By standardizing on CEL, Kyverno avoids reinventing the wheel." Platform engineers and developers are likely already familiar with CEL, as it is the same expression language used for native Kubernetes features like Custom Resource Definition (CRD) validation and admission control rules. This familiarity drastically reduces cognitive load and eliminates the context-switching required to learn and maintain a separate policy language.
This native integration is powerfully demonstrated through Kyverno's ValidatingPolicy resource. Policies are defined declaratively, with validation logic embedded directly as a CEL expression. For example, to enforce that all new namespaces must include a cost-center label, the policy is straightforward:
apiVersion: kyverno.io/v1
kind: ValidatingPolicy
metadata:
name: require-cost-center-label
spec:
validationFailureAction: Enforce
rules:
- name: check-for-cost-center
match:
any:
- resources:
kinds:
- Namespace
validate:
message: "The 'cost-center' label is required for all namespaces."
cel:
expression: "has(object.metadata.labels) && has(object.metadata.labels['cost-center'])"
The logic in the expression field is clear, concise, and immediately understandable to anyone working with Kubernetes APIs. This approach streamlines the entire policy lifecycle. By leveraging a familiar, powerful, and context-aware language, Kyverno enables faster policy authoring, simplifies debugging, and ensures greater long-term maintainability for governance at scale.
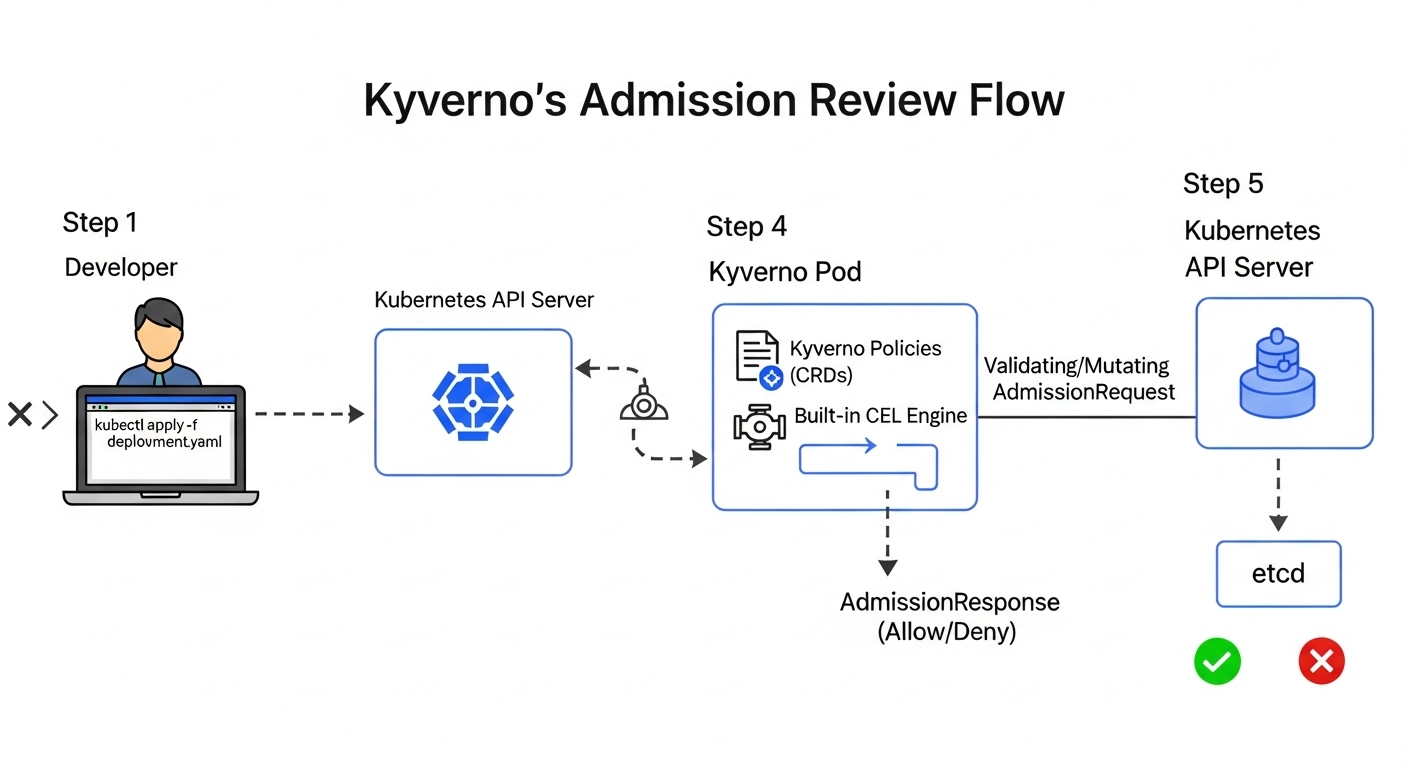
Under the Hood: The Webhook-Powered Gatekeeper
Kyverno integrates directly into the Kubernetes control plane as a dynamic admission controller, a core mechanism illustrated in the infographic above. Upon installation, Kyverno registers MutatingWebhookConfiguration and ValidatingWebhookConfiguration resources with the API server. These configurations instruct the API server to intercept relevant API requests—such as creating a new Deployment—and forward them as an AdmissionRequest payload to Kyverno’s internal webhook server.
This interception occurs before any resource is persisted to etcd. The core logic for processing these requests resides in the pkg/webhooks/resource/ directory of the Kyverno source code, where handlers evaluate the incoming resource against all matching policies. Based on the evaluation, Kyverno sends an AdmissionResponse to either allow or deny the operation, ensuring policies are enforced synchronously and in real-time.
This native webhook model is highly efficient and adds no external dependencies or complex sidecars to the control plane. You can inspect the registered webhooks with a simple command:
kubectl get validatingwebhookconfigurations -l webhooks.kyverno.io/managed-by=kyverno
By leveraging built-in Kubernetes machinery, Kyverno provides robust, real-time governance without introducing operational overhead or performance bottlenecks.
Automating at Scale: `GeneratingPolicy` for GitOps
Beyond real-time validation, Kyverno provides powerful automation capabilities through the GeneratingPolicy Custom Resource Definition. This allows platform teams to declaratively create, update, or delete Kubernetes resources in response to a trigger, such as the creation of a new Namespace. This mechanism is essential for enforcing organizational standards and reducing manual configuration.
A powerful real-world example is automatically securing new namespaces with a default-deny NetworkPolicy. The following policy generates a NetworkPolicy that blocks all ingress traffic for any newly created Namespace:
apiVersion: kyverno.io/v1
kind: GeneratingPolicy
metadata:
name: default-deny-networkpolicy
spec:
rules:
- name: generate-default-deny
match:
any:
- resources:
kinds:
- Namespace
generate:
synchronize: true
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
name: default-deny-ingress
namespace: "{{request.object.metadata.name}}"
data:
spec:
podSelector: {}
policyTypes:
- Ingress
The synchronize: true flag is the critical component for GitOps alignment. With this enabled, Kyverno not only generates the NetworkPolicy but also actively maintains its state. If a user manually alters or deletes the generated policy, Kyverno will automatically revert the change, thus correcting configuration drift and ensuring the desired state is continuously enforced. This extends the GitOps model from statically defined manifests to dynamically managed resources, a crucial capability for platform engineering teams responsible for maintaining consistency and security at scale.
The Future of Kubernetes-Native Governance
Kyverno’s architectural pillars establish it as a formidable governance solution. Its adoption of the Common Expression Language (CEL) empowers developers with a familiar, standard syntax, eliminating the friction of proprietary DSLs. The dynamic admission webhook architecture provides robust, real-time policy enforcement directly within the Kubernetes control plane, ensuring efficiency without operational overhead. Furthermore, the GeneratingPolicy resource delivers powerful automation, enabling declarative resource management and drift correction essential for modern GitOps workflows.
By deeply integrating with native Kubernetes constructs, Kyverno offers a seamless, low-friction approach to policy-as-code. For platform teams seeking to enforce security and compliance without sacrificing developer velocity, Kyverno stands out as a leading, highly integrated choice for managing complex cloud-native environments.
